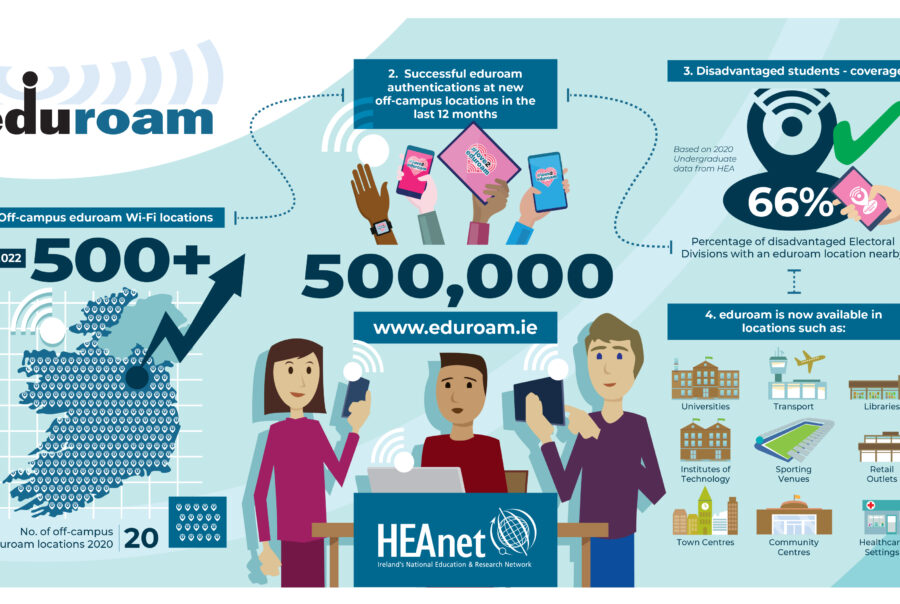
eduroam stands for education roaming.
eduroam is a Wi-Fi service which enables students, researchers and staff from participating institutions to securely access the internet at their college/university and whilst visiting other participating institutions.